Sub-netting, the meaning is there right? Dividing a network. So in brief, it is a task of dividing a network into two or smaller networks. But why? Do we actually need this? If we are doing something, there should be gain. What do we get in dividing a network?
- Increases the efficiency in routing.
What is routing in a computer network? It is a process performed by the network layer for choosing an optimal path for traffic in order to deliver the packet in a network or between or across multiple networks.
- It enhances the security of the network.
What is Network Security? The practice of preventing and protecting a network from unauthorized intrusions. It complements endpoint security, which focuses on every individual device which is connected to the network.
- Reduces the size of the broadcast domain.
What is the broadcast domain? It is a logical division of a computer network, in which all redistribution points or a communication endpoint can reach each other by a method of transferring a message to all recipients simultaneously at the data link layer.
Assume that there are two departments in a big office. Accounting and Marketing departments.
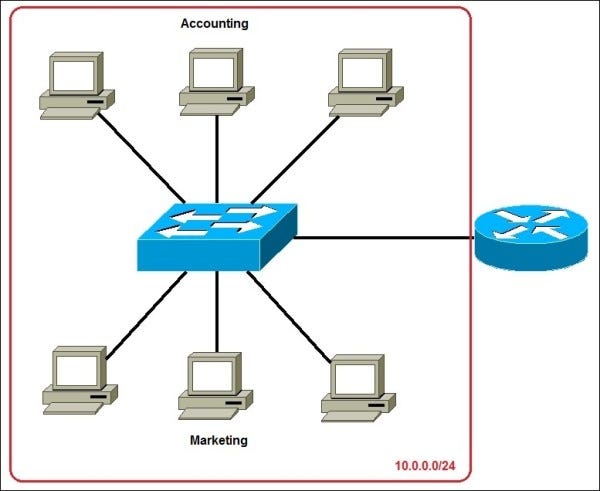
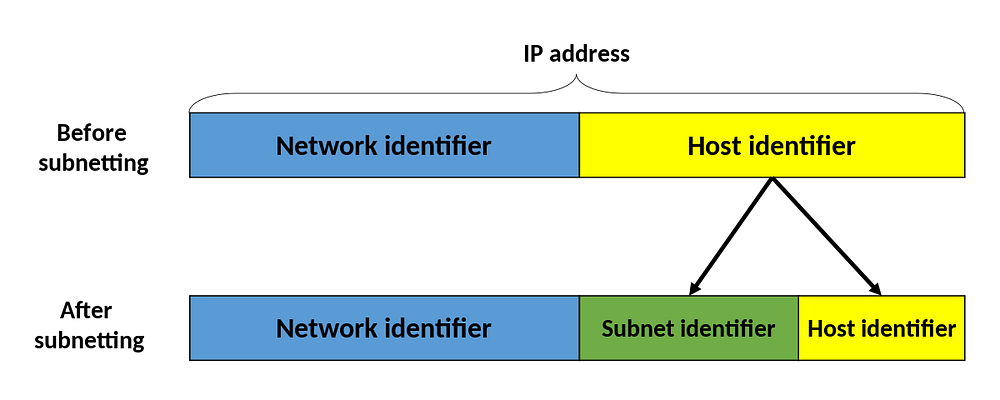
Here, all the systems are connected with a huge network 10.0.0.0/24. From this IP address, we can say that the first 24 bits are assigned as Network prefixes and the rest are assigned to the host address. Here we have not made any sub-netting. Why we can’t prefer this network in that place?
- Single broadcast domain
All hosts are in the same broadcast domain. That means, all the hosts can access a packet that was sent by one of these hosts. It is okay for a single department to share their files among themselves. But what about other departments? What is the need for the Marketing department to look into the Accounting files?
- Network security
Each device can reach any other device on the network, which can lead to security problems.
- Organizational problems
Sensitive financial data of the Accounting department shall be accessed by a host in the Marketing department.
In a large network like this, it is better to group the different departments all together as sub-nets. That is, we can group all devices from the Accounting department in the same subnet and then give access to sensitive financial data only to hosts from that sub-net.
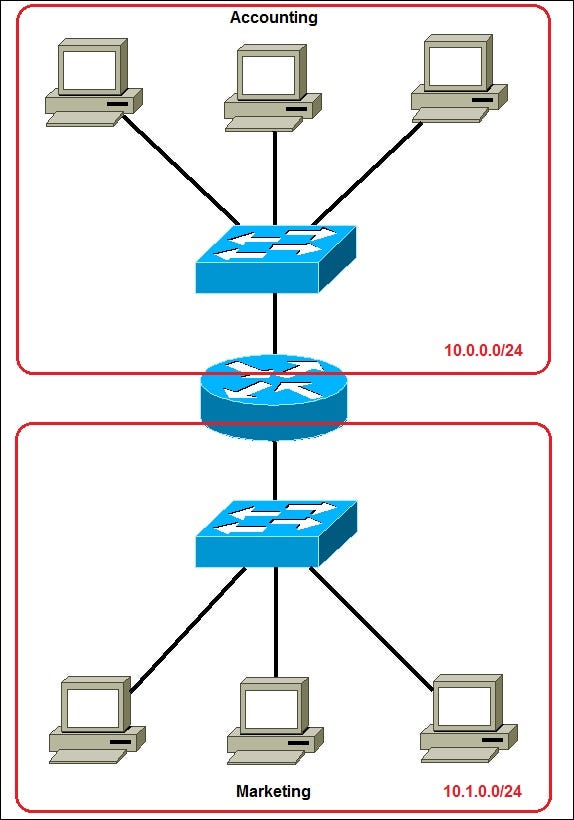
Now, you can see that two sub-nets are here for each department. Network 10.0.0.0/24 for Accounting and 10.1.0.0/24 for Marketing. Now we have devices in each sub-net that are in a different broadcast domain.
So how to sub-net a network?
Let see this through a simple example.
Assume that we have been assigned the 193.1.1.0/24 network block. We need to create sub-nets that can hold about 20 hosts in each sub-nets.
To have 20 hosts we need to find how many bits have to be assigned for host addresses. We should find the location of 20 so that it can fit into the numbers which can be written in indices form with base 2. So simply, 16 < 20 < 32. That is,
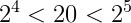
In maximum, we have to select 32 and thus we have come to a conclusion that we have to assign 5 bits for the host addresses. But the network /24 says, 8 bits are allocated for host addresses. So, we have to reduce it to 5 and those 3 bits are called sub-net bits. Altogether, 24 bits+3 bits=27 bits are named as Extended network prefixes.

The number of sub-nets available is
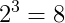
And hosts per each sub-net available is
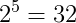
In this extended network prefix, we can create 8 sub-nets in maximum and maximum of 32 host addresses in each of those sub-nets.
The first sub-net address (#1) can be obtained when we have all 0s in the subnet bits.
#1: 1100 0001.0000 0001.0000 0001.000|_ _ _ _ _
#2: 1100 0001.0000 0001.0000 0001.001|_ _ _ _ _
#3: 1100 0001.0000 0001.0000 0001.010|_ _ _ _ _
.
.
#8: 1100 0001.0000 0001.0000 0001.111|_ _ _ _ _
.Without considering the host addresses the network mask
#1: 193.1.1.0/27
#2: 193.1.1.32/27
#3: 193.1.1.64/27
.
.
#8: 193.1.1.224/27
Each of these sub-nets will be having 32 numbers of hosts. Consider the first sub-net.
#1: 1100 0001.0000 0001.0000 0001.000|_ _ _ _ _
The first host of first sub-net (#1.1) can be obtained when all the 5 bits are 0s. That is,
#1.1: 1100 0001.0000 0001.0000 0001.000|0 0000 (193.1.1.0/27)
#1.2: 1100 0001.0000 0001.0000 0001.000|0 0001 (193.1.1.1/27)
.
.
#1.32: 1100 0001.0000 0001.0000 0001.000|1 1111 (193.1.1.31/27)
According to Internet practices, the host-number field of an IP address cannot contain all 0-bits or all 1-bits. The all 0s host-number identifies the base network (or sub-network) number, while the all 1s host-number represents the broadcast address for the network (or sub-network). So in these host addresses, we can’t use the 1st host address and the last host address.
So we can have 30 usable host addresses in each of the sub-nets. So, whenever we find the number of usable host addresses, we deduct 2 from the number of host addresses.
I hope now you’ve got an idea about sub-netting in Computer Networks.
Check it out with this simple question. List the range of host addresses that can be assigned to sub-net #3 from a network 200.35.1.0/27. You have to extend the network in order to have 50 hosts per sub-nets.
Hope this can help. Share your thoughts too.
Comments
Post a Comment